Small Business CRM Security in 2025: Protecting Your Data in a Changing Landscape
Small Business CRM Security in 2025: Protecting Your Data in a Changing Landscape
The year is 2025. Small businesses are thriving, fueled by innovation, agility, and a relentless pursuit of customer satisfaction. At the heart of many of these success stories lies a powerful tool: the Customer Relationship Management (CRM) system. It’s where businesses store crucial data – customer interactions, sales pipelines, marketing campaigns, and so much more. But with this wealth of information comes a significant responsibility: ensuring the security of that data. In this comprehensive guide, we’ll delve into the critical aspects of small business CRM security in 2025, exploring the evolving threats, the best practices for safeguarding your valuable information, and the technologies that will shape the future of data protection.
The Shifting Sands of Cyber Threats
The cybersecurity landscape is constantly evolving. What worked yesterday might be obsolete tomorrow. Small businesses, often operating with limited resources and expertise, are increasingly attractive targets for cybercriminals. In 2025, the threats have become even more sophisticated and pervasive. Here’s a look at some of the key challenges:
1. Advanced Persistent Threats (APTs)
APTs are no longer the exclusive domain of nation-states. Cybercriminals are employing highly targeted, long-term attacks designed to infiltrate systems, steal data, and remain undetected for extended periods. These attacks often exploit vulnerabilities in software, use social engineering techniques to trick employees, and employ advanced malware that can evade traditional security measures.
2. Ransomware 2.0
Ransomware continues to be a major threat, but it has evolved. Cybercriminals are not only encrypting data and demanding ransoms but are also exfiltrating sensitive information and threatening to release it publicly if the ransom isn’t paid. This double extortion tactic puts even more pressure on businesses to comply with the demands. Furthermore, ransomware-as-a-service (RaaS) is making these attacks more accessible, enabling even less sophisticated criminals to launch devastating attacks.
3. Supply Chain Attacks
Small businesses often rely on third-party vendors for various services, from cloud storage to marketing automation. Cybercriminals are increasingly targeting these vendors, knowing that compromising a single vendor can provide access to a multitude of customers. This makes it crucial to thoroughly vet and monitor all third-party providers and their security practices.
4. Phishing and Social Engineering
Despite advancements in technology, phishing remains a highly effective attack vector. Cybercriminals are becoming more adept at crafting convincing emails and messages that trick employees into revealing sensitive information or clicking on malicious links. Social engineering tactics, such as impersonating executives or technical support staff, are also on the rise.
5. AI-Powered Attacks
Artificial intelligence (AI) is a double-edged sword. While it offers powerful tools for cybersecurity, it’s also being used by cybercriminals to automate attacks, create more convincing phishing campaigns, and develop sophisticated malware that can evade detection. AI-powered bots can now scan networks for vulnerabilities, identify weak passwords, and launch attacks with unprecedented speed and efficiency.
Building a Robust CRM Security Strategy
Protecting your CRM data in 2025 requires a proactive, multi-layered approach. Here’s a comprehensive guide to building a robust security strategy:
1. Risk Assessment and Vulnerability Management
The first step is to identify your vulnerabilities. Conduct a thorough risk assessment to understand the potential threats to your CRM data and the impact of a data breach. This involves identifying all the sensitive data stored in your CRM, assessing the likelihood of various threats, and evaluating the potential damage. Regularly scan your systems for vulnerabilities, patch software promptly, and monitor your network for suspicious activity.
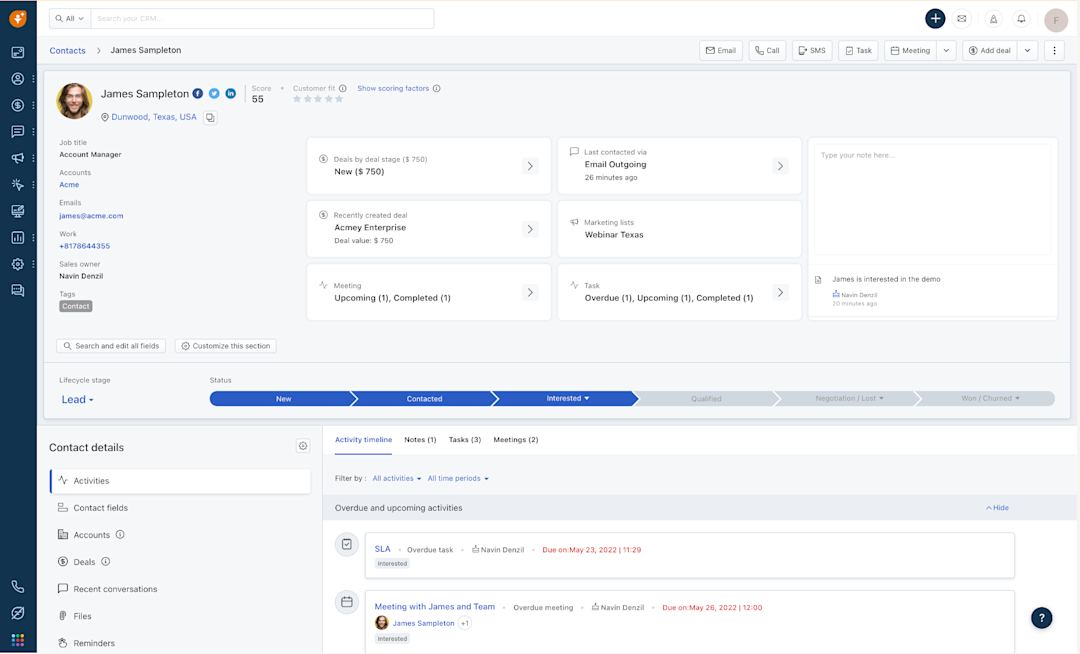
2. Access Control and Identity Management
Implement strong access controls to restrict access to your CRM data based on the principle of least privilege. Grant users only the minimum level of access necessary to perform their job duties. Use multi-factor authentication (MFA) to verify user identities and prevent unauthorized access. Regularly review user access permissions and remove access for employees who have left the company or changed roles.
3. Data Encryption
Encrypt your CRM data both at rest and in transit. Encryption protects your data from unauthorized access, even if your systems are compromised. Use strong encryption algorithms, such as AES-256, to encrypt sensitive data stored in your CRM database. Encrypt data transmitted over the network using secure protocols like HTTPS.
4. Data Backup and Disaster Recovery
Implement a comprehensive data backup and disaster recovery plan. Regularly back up your CRM data to a secure offsite location. Test your backup and recovery procedures regularly to ensure they work effectively. In the event of a data breach or system failure, you’ll need a reliable way to restore your data and minimize downtime.
5. Security Awareness Training
Your employees are your first line of defense against cyber threats. Provide regular security awareness training to educate employees about phishing, social engineering, and other common threats. Train them on how to identify suspicious emails, report security incidents, and follow security best practices. Conduct regular phishing simulations to test their awareness and identify areas for improvement.
6. Endpoint Security
Protect the devices that access your CRM data, including laptops, smartphones, and tablets. Install endpoint detection and response (EDR) solutions to detect and respond to threats on these devices. Implement mobile device management (MDM) to manage and secure mobile devices, enforce security policies, and remotely wipe data if a device is lost or stolen.
7. Network Security
Secure your network infrastructure to prevent unauthorized access to your CRM data. Use a firewall to filter network traffic and block malicious activity. Implement intrusion detection and prevention systems (IDPS) to detect and respond to network attacks. Regularly update your network security devices with the latest security patches.
8. CRM Vendor Security
Choose a CRM vendor that prioritizes security. Review the vendor’s security policies, certifications, and data protection practices. Ensure that the vendor uses strong encryption, provides regular security updates, and has a robust incident response plan. Consider using a CRM that offers features like data loss prevention (DLP) and security information and event management (SIEM).
9. Compliance and Governance
Ensure that your CRM security practices comply with relevant regulations, such as GDPR, CCPA, and HIPAA. Establish a clear governance framework that defines roles, responsibilities, and procedures for managing CRM security. Regularly audit your security practices to ensure they are effective and compliant.
Emerging Technologies Shaping CRM Security in 2025
The future of CRM security is being shaped by several emerging technologies:
1. Artificial Intelligence and Machine Learning
AI and machine learning are playing an increasingly important role in cybersecurity. AI-powered security solutions can detect and respond to threats in real-time, analyze large datasets to identify patterns and anomalies, and automate security tasks. AI can also be used to improve user authentication, detect phishing attempts, and predict potential security breaches.
2. Blockchain Technology
Blockchain technology offers a secure and transparent way to store and manage data. It can be used to protect CRM data from tampering and ensure data integrity. Blockchain can also be used to create secure and verifiable audit trails, making it easier to track and monitor data access and changes.
3. Zero Trust Architecture
Zero Trust is a security model that assumes no user or device can be trusted by default, whether inside or outside the network perimeter. It requires all users and devices to be authenticated and authorized before accessing any resources. Zero Trust architecture can help prevent lateral movement by attackers and limit the impact of a data breach.
4. Extended Detection and Response (XDR)
XDR solutions integrate security data from multiple sources, such as endpoints, networks, and cloud applications, to provide a unified view of security threats. XDR can detect and respond to threats more effectively than traditional security solutions, providing a more holistic approach to security.
5. Quantum-Resistant Cryptography
With the advent of quantum computing, traditional encryption algorithms are becoming vulnerable. Quantum-resistant cryptography uses algorithms that are resistant to attacks from quantum computers. Implementing quantum-resistant cryptography will be crucial to protecting sensitive CRM data in the future.
Choosing the Right CRM Security Solutions for Your Business
Selecting the right CRM security solutions for your small business can be a daunting task. Here are some tips to help you make the right choices:
- Assess Your Needs: Identify your specific security requirements based on your business size, industry, and the type of data you store in your CRM.
- Research Vendors: Research different CRM security vendors and compare their features, pricing, and customer reviews.
- Consider Integration: Choose solutions that integrate seamlessly with your existing CRM and other business systems.
- Prioritize Usability: Select solutions that are easy to use and manage, even for non-technical users.
- Look for Scalability: Choose solutions that can scale to meet your growing business needs.
- Evaluate Support: Ensure that the vendor offers adequate support and training.
- Get Expert Advice: If needed, consult with a cybersecurity expert to help you choose the right solutions.
The Human Factor: Cultivating a Security-Conscious Culture
Technology alone is not enough to ensure CRM security. The human factor is crucial. It’s essential to cultivate a security-conscious culture within your organization. This involves:
- Training and Education: Provide regular security awareness training to all employees, covering topics such as phishing, social engineering, password security, and data privacy.
- Clear Policies and Procedures: Establish clear security policies and procedures that employees must follow.
- Regular Communication: Communicate regularly with employees about security threats and best practices.
- Reporting and Incident Response: Establish a clear process for reporting security incidents and responding to them promptly.
- Positive Reinforcement: Recognize and reward employees who demonstrate good security practices.
The Future is Now: Preparing for CRM Security in 2025
The challenges and opportunities of CRM security in 2025 are significant. Small businesses that prioritize security and proactively implement the strategies and technologies outlined in this guide will be better positioned to protect their valuable data, build customer trust, and thrive in the years to come. It’s not just about protecting data; it’s about building a resilient and secure business that can weather the storms of the digital age.
By embracing a proactive approach to security, staying informed about emerging threats, and investing in the right technologies and training, your small business can navigate the complexities of the cybersecurity landscape and safeguard its most valuable asset: its customer data.
The future of CRM security is not just about technology; it’s about people, processes, and a commitment to continuous improvement. By embracing these principles, small businesses can build a secure and resilient future, poised for success in the ever-evolving world of customer relationship management.
In conclusion, securing your CRM in 2025 requires a multifaceted approach. From understanding the latest threats like APTs and ransomware to implementing robust security measures such as encryption and multi-factor authentication, the steps are crucial. Remember to choose a CRM provider with strong security practices and always prioritize employee training, building a security-conscious culture. By staying vigilant, adapting to new technologies like AI and XDR, and following these guidelines, small businesses can confidently protect their customer data and thrive in the future.