Small Business CRM Demo: See How to Skyrocket Your Sales and Customer Satisfaction
Introduction: The Power of a CRM for Small Businesses
Running a small business is a whirlwind of activity. You’re juggling everything from marketing and sales to customer service and operations. In the midst of this, it’s easy for things to slip through the cracks. That’s where a Customer Relationship Management (CRM) system comes in. Think of it as your central hub for all things customer-related. A well-implemented CRM can be the difference between surviving and thriving.
This article dives deep into the world of small business CRM demos. We’ll explore what a CRM is, why you need one, and what to look for in a demo. We’ll also walk you through the key features and benefits, and provide insights to help you choose the perfect CRM for your specific needs. Get ready to transform your business!
What is a CRM System? A Simple Explanation
At its core, a CRM system is a software solution that helps businesses manage their interactions with current and potential customers. It’s much more than just a contact list; it’s a comprehensive platform that allows you to:
- Centralize Customer Data: Store all customer information in one place, including contact details, purchase history, communication logs, and more.
- Improve Communication: Track all interactions with customers, ensuring consistent and personalized communication across all channels.
- Automate Tasks: Automate repetitive tasks like sending emails, scheduling appointments, and follow-ups.
- Analyze Data: Gain valuable insights into customer behavior and sales performance through reporting and analytics.
- Enhance Collaboration: Enable your team to work together more effectively by sharing information and coordinating efforts.
In essence, a CRM system helps you build stronger customer relationships, improve sales, and boost overall business efficiency. It’s a critical tool for any small business looking to scale and succeed.
Why Your Small Business Needs a CRM
You might be thinking, “I’m a small business, do I really need a CRM?” The answer is a resounding YES! Here’s why:
- Improved Organization: Say goodbye to scattered spreadsheets and lost contact information. A CRM keeps everything organized and accessible.
- Increased Sales: By tracking leads, managing the sales pipeline, and automating follow-ups, a CRM can significantly boost your sales numbers.
- Enhanced Customer Service: Provide personalized and responsive customer service by having all customer information readily available.
- Better Marketing: Segment your customer base and tailor your marketing campaigns for maximum impact.
- Time Savings: Automate repetitive tasks, freeing up your team to focus on more important activities.
- Data-Driven Decisions: Make informed decisions based on real-time data and analytics.
Even if you’re just starting out, a CRM can help you lay the foundation for future growth. It’s an investment that pays off in the long run.
Key Features to Look for in a CRM Demo
When you’re evaluating CRM systems, watching a demo is crucial. It gives you a hands-on look at the software and allows you to see if it’s the right fit for your business. Here are some key features to pay attention to during a CRM demo:
1. Contact Management
This is the heart of any CRM. The demo should clearly show how the system allows you to:
- Store and organize contact information: including names, addresses, phone numbers, email addresses, and social media profiles.
- Segment contacts: based on various criteria, such as demographics, purchase history, or lead source.
- Import and export contacts: easily transfer your existing contact data into the CRM.
- View contact history: see all interactions with a contact in one place.
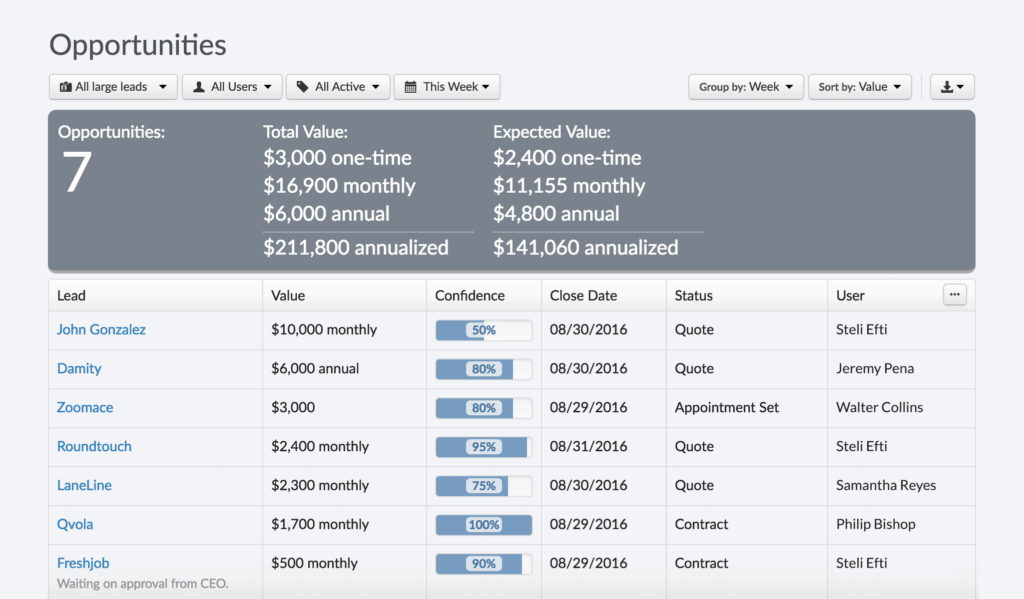
2. Sales Pipeline Management
A good CRM should streamline your sales process. Look for a demo that demonstrates how the system allows you to:
- Track leads: from initial contact to closed deal.
- Manage deals: including stages, values, and close dates.
- Automate sales tasks: such as sending follow-up emails and scheduling appointments.
- Generate sales reports: track your sales performance and identify areas for improvement.
3. Marketing Automation
Many CRM systems offer marketing automation features. During the demo, look for how the CRM can help you:
- Create and send email campaigns: including newsletters, promotions, and automated sequences.
- Segment your audience: based on their behavior and interests.
- Track campaign performance: measure open rates, click-through rates, and conversions.
- Integrate with social media: manage your social media presence and engage with your audience.
4. Customer Service and Support
A CRM should enhance your customer service capabilities. The demo should showcase how the system allows you to:
- Track customer inquiries: manage support tickets and ensure timely responses.
- Provide self-service options: such as knowledge bases and FAQs.
- Monitor customer satisfaction: gather feedback and identify areas for improvement.
- Integrate with other support channels: such as live chat and phone support.
5. Reporting and Analytics
Data is king! The demo should highlight the CRM’s reporting and analytics capabilities, including:
- Customizable dashboards: to visualize key metrics and track performance.
- Pre-built reports: for sales, marketing, and customer service.
- Data export options: to share data with other systems or stakeholders.
- Real-time insights: to make data-driven decisions.
6. Integrations
Consider how well the CRM integrates with your existing tools. The demo should show integrations with:
- Email marketing platforms: such as Mailchimp or Constant Contact.
- Accounting software: such as QuickBooks or Xero.
- Project management tools: such as Asana or Trello.
- Other business applications: that you use on a daily basis.
7. User Interface (UI) and User Experience (UX)
Finally, pay attention to the overall usability of the CRM. Is it easy to navigate? Is the interface clean and intuitive? Look for:
- A user-friendly interface: that is easy to learn and use.
- Customization options: to tailor the system to your specific needs.
- Mobile accessibility: to access your CRM data on the go.
- Excellent customer support: in case you need help.
How to Prepare for a Small Business CRM Demo
To get the most out of a CRM demo, it’s important to prepare beforehand. Here’s a step-by-step guide:
1. Identify Your Needs and Goals
Before you start watching demos, take some time to define your business needs and goals. What are you hoping to achieve with a CRM? What are your pain points? What features are most important to you?
- Identify your business objectives: e.g., increase sales, improve customer satisfaction, streamline operations.
- List your current challenges: e.g., disorganized data, missed follow-ups, poor communication.
- Prioritize your requirements: What are the must-have features? What are the nice-to-haves?
2. Research CRM Providers
Once you have a clear understanding of your needs, start researching CRM providers. Look for vendors that specialize in small businesses and offer the features you need. Read reviews, compare pricing, and create a shortlist of potential candidates.
- Read online reviews: from other small businesses.
- Compare pricing plans: and choose the one that fits your budget.
- Check for free trials or demos: to test the software before you commit.
3. Prepare Questions to Ask
Don’t just passively watch the demo. Come prepared with a list of questions to ask the vendor. This will help you assess the CRM’s capabilities and determine if it’s the right fit for your business.
- Ask about specific features: that are important to you.
- Inquire about integrations: with your existing tools.
- Ask about pricing and support: including training and onboarding.
- Ask about data migration: to ensure a smooth transition.
4. Evaluate the Demo
During the demo, take notes and evaluate the CRM based on your pre-defined criteria. Does it meet your needs? Is it easy to use? Does it integrate with your existing tools?
- Focus on the features that matter most to you:
- Assess the user interface and user experience:
- Consider the overall value: for the price.
5. Follow Up After the Demo
After the demo, follow up with the vendor to ask any remaining questions and get a price quote. If you’re still unsure, consider requesting a free trial or a second demo. Make a decision based on your research and evaluation.
- Ask for a price quote:
- Request a free trial: if available.
- Make a final decision: based on your evaluation.
Top CRM Systems for Small Businesses (with demo considerations)
Here’s a look at some popular CRM systems suitable for small businesses, along with what to look for in their demos:
1. HubSpot CRM
Why it’s a good choice: HubSpot offers a free CRM plan with powerful features, making it ideal for startups and small businesses on a budget. It’s known for its ease of use and comprehensive marketing automation capabilities.
What to look for in the demo:
- Ease of use: See how quickly you can navigate the interface and find the information you need.
- Marketing automation: Explore the email marketing, lead nurturing, and landing page creation features.
- Sales pipeline management: Observe how the system helps you track deals and manage your sales process.
- Integrations: Check out integrations with other popular tools like Gmail, Outlook, and social media platforms.
2. Zoho CRM
Why it’s a good choice: Zoho CRM offers a wide range of features and customization options, making it suitable for businesses of all sizes. It’s known for its affordability and its ability to integrate with other Zoho apps.
What to look for in the demo:
- Customization: See how you can tailor the CRM to your specific business needs.
- Sales force automation: Explore the features that help you automate your sales tasks and improve efficiency.
- Reporting and analytics: Check out the dashboards and reports to see how you can track your performance.
- Integrations: Look for integrations with other Zoho apps and third-party applications.
3. Freshsales
Why it’s a good choice: Freshsales is a sales-focused CRM that’s known for its user-friendly interface and powerful features. It’s a good option for businesses that want to streamline their sales process and close more deals.
What to look for in the demo:
- Sales automation: Observe how the system helps you automate your sales tasks and improve efficiency.
- Lead scoring: See how the system helps you prioritize your leads and focus on the most promising ones.
- Phone integration: Check out the features that allow you to make and receive calls directly from the CRM.
- Reporting and analytics: Explore the dashboards and reports to see how you can track your sales performance.
4. Pipedrive
Why it’s a good choice: Pipedrive is a sales-focused CRM that’s designed to help salespeople close more deals. It’s known for its visual pipeline and its ease of use.
What to look for in the demo:
- Visual pipeline: See how the system helps you visualize your sales process and track your deals.
- Deal management: Explore the features that allow you to manage your deals and move them through the pipeline.
- Automation: Check out the features that help you automate your sales tasks and improve efficiency.
- Reporting and analytics: See how the system helps you track your sales performance and identify areas for improvement.
5. Insightly
Why it’s a good choice: Insightly is a CRM and project management tool that’s designed to help small businesses manage their sales, marketing, and projects in one place. It’s known for its ease of use and its affordable pricing.
What to look for in the demo:
- Contact management: See how the system helps you manage your contacts and track your interactions.
- Sales pipeline management: Observe how the system helps you track your deals and manage your sales process.
- Project management: Check out the features that allow you to manage your projects and track your progress.
- Reporting and analytics: Explore the dashboards and reports to see how you can track your performance.
Making the Right Choice: Key Considerations
Choosing the right CRM is a significant decision. Here are some key factors to consider to ensure you make the best choice for your small business:
- Business Needs and Goals: Align your CRM selection with your specific goals. Do you need to increase sales, improve customer service, or streamline marketing?
- Budget: CRM pricing varies significantly. Consider your budget and choose a system that offers the features you need at a price you can afford. Factor in not just the monthly fee, but also potential setup costs, training, and any add-ons.
- Ease of Use: The CRM should be user-friendly and easy to navigate. A complex system will be difficult for your team to adopt, hindering its effectiveness. Prioritize intuitive interfaces and simple workflows.
- Scalability: Choose a CRM that can grow with your business. As your company expands, you’ll need a system that can handle more data, users, and features.
- Integrations: Consider how well the CRM integrates with your existing tools, such as email marketing platforms, accounting software, and other business applications. Seamless integration will save you time and effort.
- Customer Support: Make sure the CRM provider offers excellent customer support. This includes training resources, documentation, and responsive support channels to help you with any issues.
- Data Migration: Consider the ease of migrating your existing data into the new CRM. The vendor should provide tools or assistance to help you transfer your data smoothly.
- Mobile Accessibility: Ensure the CRM has a mobile app or is accessible on mobile devices. This will allow your team to access and update data on the go.
- Security: Choose a CRM provider with robust security measures to protect your sensitive customer data. Look for features like data encryption, secure access controls, and regular security audits.
Implementation and Beyond: Getting the Most Out of Your CRM
Once you’ve chosen a CRM, the real work begins: implementation. Here’s a guide to help you get started and maximize your CRM’s value:
1. Data Migration
Carefully transfer your existing customer data into the CRM. This may involve importing data from spreadsheets, databases, or other systems. Ensure data accuracy and consistency during the migration process. Clean up any duplicate or outdated data.
2. Training and Onboarding
Provide thorough training to your team on how to use the CRM. Offer different training levels based on roles and responsibilities. Create user guides, tutorials, and FAQs to support ongoing learning. Encourage adoption by highlighting the benefits of the CRM and demonstrating its value.
3. Customization and Configuration
Customize the CRM to fit your specific business needs. This may involve configuring fields, workflows, and reports. Set up user roles and permissions to control access to data. Tailor the system to your sales process, marketing campaigns, and customer service operations.
4. Integration with Other Systems
Integrate the CRM with your existing tools to streamline your workflows. This could include email marketing platforms, accounting software, and other business applications. Data synchronization will eliminate manual data entry and improve data accuracy.
5. Ongoing Monitoring and Optimization
Continuously monitor your CRM usage and performance. Track key metrics such as sales growth, customer satisfaction, and marketing campaign effectiveness. Identify areas for improvement and optimize your CRM configuration and workflows. Regularly review and update your CRM strategy to adapt to changing business needs.
6. Data Security and Compliance
Implement robust security measures to protect your customer data. This includes data encryption, access controls, and regular security audits. Ensure your CRM practices comply with relevant data privacy regulations such as GDPR and CCPA.
Conclusion: Embrace the Power of CRM
Investing in a CRM system is a game-changer for small businesses. By centralizing customer data, streamlining processes, and providing valuable insights, a CRM empowers you to build stronger customer relationships, boost sales, and drive sustainable growth. Take the time to research and choose the right CRM for your business, prepare thoroughly for the demo, and ensure successful implementation. With the right CRM in place, you’ll be well-equipped to thrive in today’s competitive market.
Remember, the journey doesn’t end with implementation. Continuously monitor your CRM’s performance, optimize your workflows, and adapt to changing business needs. By embracing the power of CRM, you can unlock the full potential of your small business and achieve long-term success.