Small Business CRM Enhancements: What to Expect and How to Prepare in 2025

Small Business CRM Enhancements: Navigating the Future in 2025
The world of customer relationship management (CRM) is constantly evolving, and for small businesses, staying ahead of the curve is crucial. As we approach 2025, significant enhancements are on the horizon, promising to reshape how small businesses interact with their customers, manage data, and drive growth. This article delves into the anticipated CRM enhancements, providing a roadmap for small business owners to prepare for and leverage these advancements.
Understanding the Landscape: Why CRM Matters for Small Businesses
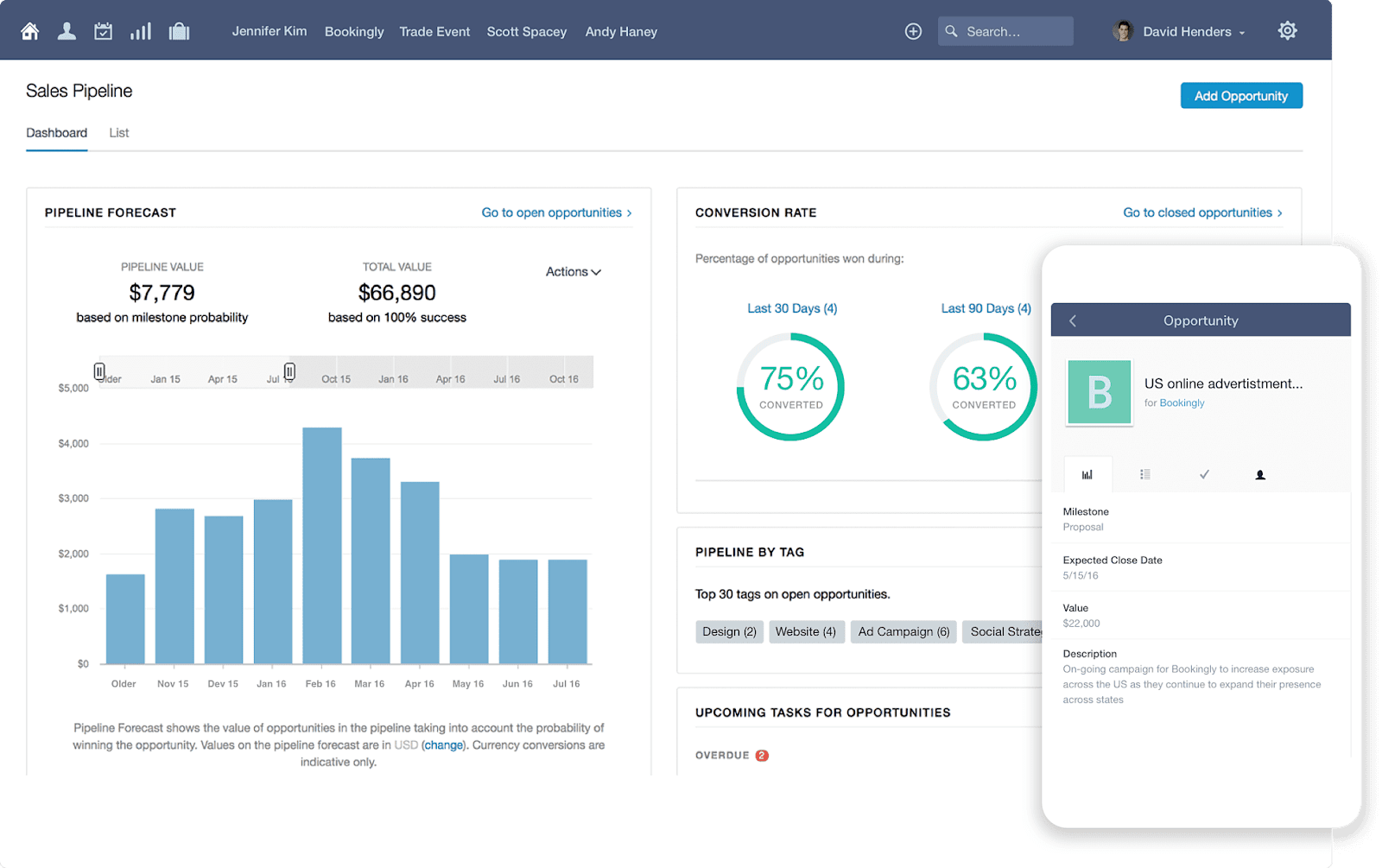
Before we explore the future, let’s revisit the fundamentals. A CRM system is more than just a contact database; it’s the backbone of a customer-centric business strategy. For small businesses, CRM offers a powerful suite of tools to:
- Centralize Customer Data: Consolidate all customer interactions, preferences, and purchase history in one accessible location.
- Improve Customer Service: Provide personalized and responsive support, leading to higher customer satisfaction.
- Streamline Sales Processes: Automate tasks, track leads, and close deals more efficiently.
- Enhance Marketing Efforts: Segment audiences, personalize campaigns, and measure marketing ROI.
- Boost Productivity: Automate repetitive tasks, freeing up employees to focus on core business activities.
In today’s competitive landscape, small businesses need every advantage they can get. A well-implemented CRM system is no longer a luxury; it’s a necessity.
Key CRM Enhancements to Anticipate in 2025
The CRM landscape is poised for significant transformations. Here’s a glimpse into the key enhancements expected by 2025:
1. Artificial Intelligence (AI) and Machine Learning (ML) Integration
AI and ML are already making their mark on CRM, and their influence will only intensify. By 2025, we can expect:
- Predictive Analytics: CRM systems will become even better at predicting customer behavior, identifying potential churn, and recommending personalized offers.
- Automated Task Management: AI-powered automation will handle more routine tasks, such as data entry, email responses, and lead scoring.
- Personalized Customer Interactions: AI will enable more sophisticated personalization across all customer touchpoints, from website interactions to sales calls.
- Sentiment Analysis: AI will analyze customer communications to gauge sentiment, providing valuable insights into customer satisfaction and areas for improvement.
For small businesses, this means a more proactive and responsive approach to customer engagement. AI-driven insights will help businesses anticipate customer needs and provide exceptional service.
2. Enhanced Automation and Workflow Optimization
Automation is a cornerstone of CRM, and in 2025, we’ll see even more sophisticated automation capabilities. Expect to see:
- Advanced Workflow Automation: Complex workflows will be automated, streamlining processes across sales, marketing, and customer service.
- Intelligent Task Assignment: Systems will automatically assign tasks to the most qualified team members based on skills, availability, and workload.
- Integration with More Tools: Seamless integration with a wider range of business tools, such as accounting software, project management platforms, and communication tools.
- Robotic Process Automation (RPA): RPA will automate repetitive tasks that previously required human intervention, further boosting efficiency.
This level of automation will free up valuable time for small business owners and their teams, allowing them to focus on strategic initiatives and customer relationships.
3. Improved Mobile CRM and Accessibility
Mobile CRM is already essential, but its importance will grow exponentially. In 2025, expect:
- More Robust Mobile Apps: CRM mobile apps will offer the same functionality as desktop versions, with enhanced features and a better user experience.
- Offline Access: The ability to access and update customer data even without an internet connection.
- Voice-Activated Commands: Voice commands will allow users to update records, schedule tasks, and access information hands-free.
- Geolocation Features: Integration with GPS and location-based services to track customer interactions and optimize sales routes.
This will allow small business owners and their teams to stay connected with customers and manage their businesses from anywhere, anytime.
4. Enhanced Data Security and Privacy Features
Data security and privacy are paramount. In 2025, CRM systems will prioritize:
- Advanced Encryption: Enhanced encryption methods to protect sensitive customer data.
- Compliance with Regulations: Adherence to evolving data privacy regulations, such as GDPR and CCPA.
- Granular Permissions: More control over user access and data visibility.
- Proactive Threat Detection: AI-powered tools to detect and prevent data breaches.
This will provide peace of mind and ensure that customer data is protected from cyber threats.
5. Increased Focus on Customer Experience (CX)
Customer experience is becoming the ultimate differentiator. By 2025, CRM systems will:
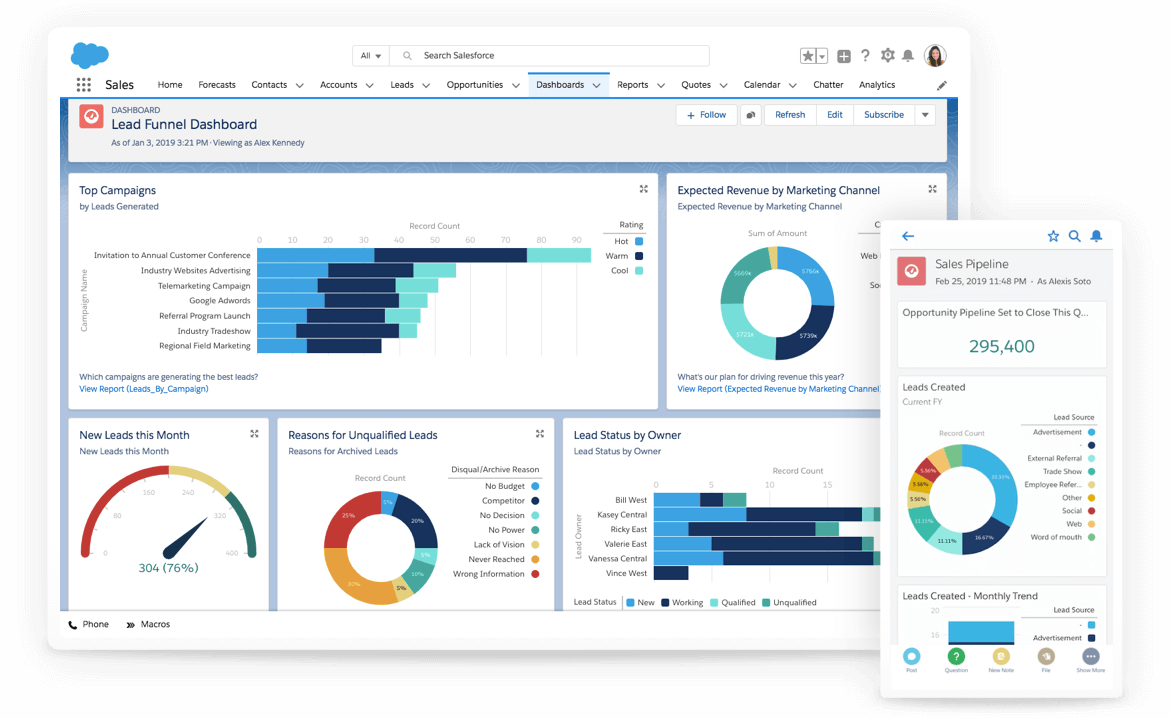
- Offer More CX Analytics: Deeper insights into the customer journey, identifying pain points and opportunities for improvement.
- Enable Omnichannel Communication: Seamless communication across multiple channels, including email, phone, social media, and live chat.
- Personalized Customer Portals: Self-service portals that allow customers to manage their accounts, access support, and track their orders.
- Proactive Customer Service: Proactive outreach and support based on customer behavior and preferences.
This will help small businesses create loyal customers and build a strong brand reputation.
Preparing Your Small Business for CRM Enhancements in 2025
Preparing for these enhancements requires a proactive approach. Here’s how small businesses can get ready:
1. Assess Your Current CRM System
Before making any changes, evaluate your current CRM system. Ask yourself:
- Is it meeting your current needs?
- Does it integrate with other business tools?
- Is it scalable to accommodate future growth?
- Are you utilizing all its features?
Identify any shortcomings and areas for improvement. This assessment will guide your decision-making process.
2. Research and Evaluate CRM Options
Explore the market to identify CRM systems that align with your business needs and budget. Consider:
- Features and Functionality: Does the system offer the features you need, such as sales automation, marketing automation, and customer service tools?
- Integration Capabilities: Does it integrate with your existing tools, such as email marketing platforms, accounting software, and social media channels?
- Scalability: Can the system scale to accommodate your future growth?
- Pricing: Does the pricing model fit your budget?
- Ease of Use: Is the system user-friendly and easy to learn?
- Customer Support: Does the vendor offer adequate customer support?
Read reviews, request demos, and compare different systems to find the best fit for your business.
3. Invest in Training and Education
Ensure that your team is properly trained on the new CRM system and its features. Consider:
- Training Programs: Provide comprehensive training programs to familiarize your team with the system.
- Documentation: Create user manuals and documentation to guide users.
- Ongoing Support: Provide ongoing support and training to help users stay up-to-date on the latest features and best practices.
Investing in training will maximize the value of your CRM system.
4. Plan for Data Migration
If you’re switching CRM systems, plan for data migration carefully. This involves:
- Data Cleaning: Clean and organize your existing data to ensure accuracy.
- Data Mapping: Map your data fields from your old system to your new system.
- Data Migration Tools: Use data migration tools to automate the process.
- Testing: Test the data migration process to ensure that all data is transferred correctly.
A smooth data migration is essential for a successful CRM implementation.
5. Embrace a Customer-Centric Culture
A CRM system is only as effective as the culture that supports it. Foster a customer-centric culture within your business by:
- Prioritizing Customer Needs: Put your customers’ needs at the center of your business decisions.
- Empowering Your Team: Empower your team to provide exceptional customer service.
- Soliciting Customer Feedback: Regularly solicit customer feedback to identify areas for improvement.
- Using Data to Drive Decisions: Use CRM data to make informed decisions about your business.
A customer-centric culture will enhance the effectiveness of your CRM system and drive customer loyalty.
6. Stay Informed and Adaptable
The CRM landscape is constantly evolving. Stay informed about the latest trends and technologies by:
- Reading Industry Publications: Subscribe to industry publications and blogs to stay up-to-date on the latest developments.
- Attending Webinars and Conferences: Attend webinars and conferences to learn from experts and network with other professionals.
- Experimenting with New Features: Experiment with new features and technologies to see how they can benefit your business.
- Being Adaptable: Be prepared to adapt your CRM strategy as the technology evolves.
By staying informed and adaptable, you can ensure that your CRM system remains effective and relevant.
Choosing the Right CRM for Your Small Business in 2025
Selecting the right CRM system is crucial for leveraging the enhancements of 2025. Consider the following when making your decision:
1. Scalability
Choose a CRM that can grow with your business. Ensure it can handle increasing numbers of contacts, users, and data without performance issues.
2. Integration
Prioritize a CRM that integrates seamlessly with your existing tools, such as email marketing platforms, accounting software, and communication tools. This streamlines your workflows and reduces manual data entry.
3. Ease of Use
Opt for a user-friendly CRM with an intuitive interface. This reduces the learning curve for your team and ensures they adopt the system quickly.
4. Mobile Capabilities
Ensure the CRM offers robust mobile apps that provide full functionality on the go. This allows your team to stay connected and productive from anywhere.
5. Customization
Choose a CRM that allows you to customize fields, workflows, and reports to meet your specific business needs. This ensures the system aligns with your unique processes.
6. Pricing and Value
Compare pricing models and assess the value offered by each CRM. Consider the features, support, and scalability to determine the best return on investment.
7. Vendor Reputation
Research the CRM vendor’s reputation and customer support. Read reviews, check references, and ensure they have a track record of providing excellent service.
The Impact of CRM Enhancements on Small Business Growth
The CRM enhancements of 2025 will have a profound impact on small business growth. Here’s how:
1. Increased Efficiency and Productivity
Automation, streamlined workflows, and improved data management will free up your team’s time, allowing them to focus on core business activities and strategic initiatives.
2. Improved Customer Relationships
Personalized interactions, proactive customer service, and omnichannel communication will enhance customer satisfaction and build stronger relationships.
3. Higher Sales and Revenue
AI-powered insights, predictive analytics, and targeted marketing campaigns will help you identify leads, close deals, and drive revenue growth.
4. Better Decision-Making
Data-driven insights and analytics will empower you to make informed decisions about your business, leading to better outcomes.
5. Enhanced Competitive Advantage
By leveraging the latest CRM enhancements, you can gain a competitive edge in the market and attract and retain customers.
Conclusion: Embracing the Future of CRM
The CRM landscape is undergoing a significant transformation, and small businesses that embrace these enhancements will be well-positioned for success in 2025 and beyond. By understanding the key trends, preparing your business, and choosing the right CRM system, you can unlock the full potential of customer relationship management and drive sustainable growth. The future of CRM is bright, and the opportunities for small businesses are immense. By proactively adapting and embracing these changes, you can ensure your business thrives in the years to come. Don’t just keep up; get ahead. The time to prepare for the future of CRM is now.